CVE-2023-5830: Critical Security Vulnerability in ColumbiaSoft Document Locator
Disclaimer: This information is being published for educational purposes only
Background
With the help of my colleague @micahvandeusen, in the late-summer of 2022 we identified and exploited a critical security vulnerability present within ColumbiaSoft's Document Locator application. This vulnerability specifically targets the client-side Server: parameter of the /api/authentication/login endpoint within the WebTools component. The nature of this flaw allows attackers to manipulate the Server: argument and effectively perform an SSRF-style attack where it is possible to receive administrative credentials to the Document Locator application instance resulting in full compromise of the data stored within.
Description of the Vulnerability
As mentioned previously, This vulnerability specifically targets the client-side Server: parameter of the /api/authentication/login endpoint within the WebTools component. By manipulating this parameter it is possible to confirm out-of-band interactions such as external DNS interactions with an arbitrary domain.
Furthermore, in conjunction with manipulating the Server: parameter, modifying the LoginType: parameter to a value of "differentwindows" can lead to a properly positioned attacker receiving clear-text administrative credentials over the MSSQL protocol. More details on exploitation can be found below.
Risk and Impact
The risk associated with CVE-2023-5830 is classified as critical with a CVSS 3.0 Base score of 9.8 due to the potential for trivial unauthorized access. Exploitation of this vulnerability can be carried out remotely, from an unauthenticated perspective and is trivial to exploit with standard tooling such as Burp Suite, Interactsh (Or burp collaborator) and Responder.
The impact of exploitation is significant as it can lead to a compromise of the integrity and confidentiality of the data managed by ColumbiaSoft Document Locator application. Given the application's role in managing sensitive documents, the exploitation of this vulnerability could have far-reaching implications for affected organizations, including data breaches and unauthorized access to confidential information.
Mitigation Strategies
In response to the discovery of CVE-2023-5830, ColumbiaSoft has released updates to mitigate this vulnerability. Specifically, upgrading to version 7.2 SP4 or 2021.1 of the Document Locator is recommended to address the security flaw effectively.
Detection
Security engineers and penetration testers can test for this vulnerability by leveraging a Nuclei template I've created here. Example execution of this template is seen below
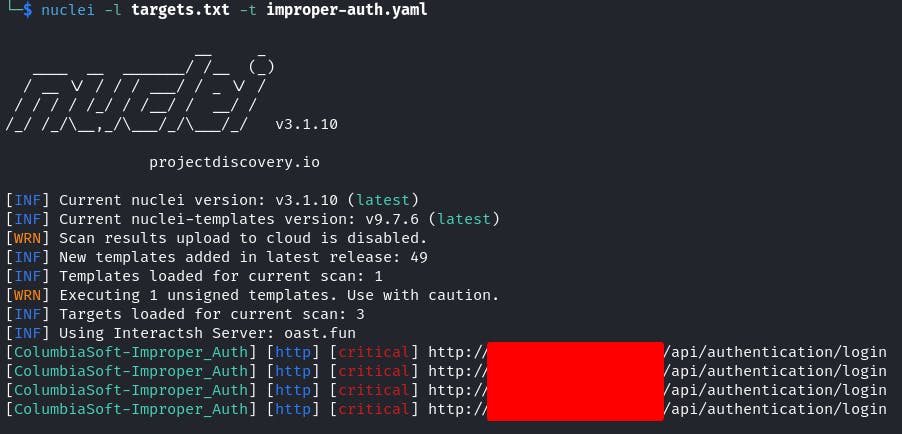
Recommendations for Users
For organizations and individuals utilizing ColumbiaSoft Document Locator, it is imperative to promptly apply the recommended updates to mitigate the risks associated with CVE-2023-5830. Upgrading to the specified versions not only addresses this critical vulnerability but also enhances the overall security posture of the document management system.
Exploitation
Exploitation of this vulnerability is fairly simple. After identification of an application instance, capture an HTTP POST request submitted to the application in Burp suite from the login page as shown below..
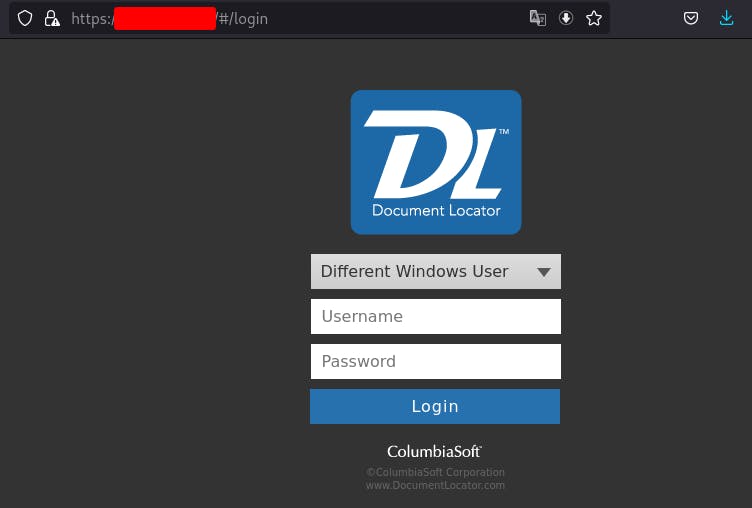
After capturing the authentication request using Burp Suite's intercept module, modify the Server: parameter and paste in either a Burp Collaborator payload or an interactsh payload (in this case interactsh was used) to test for OOB DNS interaction.
Interactsh can be used to generate a URL for observing OOB interaction.
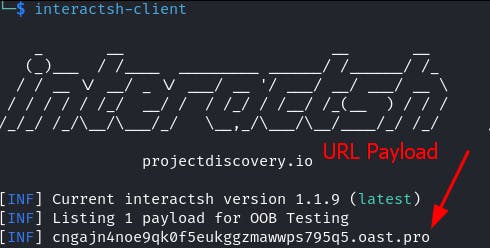
Change the Server: parameter in the request to contain the interactsh payload.

With the payload set, submit the authentication request in Burp Suite. Seen below are two DNS interactions received after submission of the authentication request.
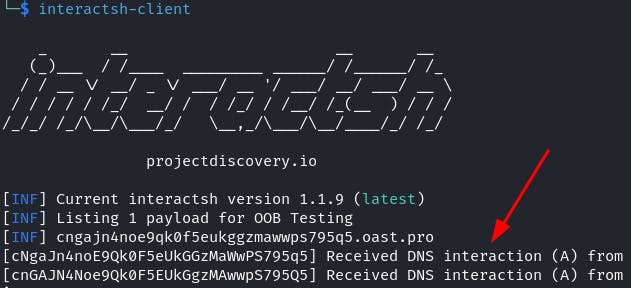
With external DNS interaction confirmed, compromise of the application can be achieved by configuring a publicly accessible machine/VM. Services such as an AWS EC2 or Google Cloud Compute Engine can be used for this. On the publicly accessible system, ensure that an ingress firewall rule allowing TCP 1433/MSSQL traffic is enabled. Additionally, to capture the authentication request, the tool Responder should be installed.
After configuring a publicly available system, run Responder in analyze mode
With Responder running, make note of the Public IPv4 address of your system and replace the value of the Server: parameter with the IP of your system.

Now submit the authentication and you should receive cleartext administrative credentials that can be used to login to the application

As you can see, this is a pretty critical vulnerability that warrants a CVSS score of 9.8. At the time of this writing no public PoC is known aside from the Nuclei template created for detection opportunities.

